Better solutions for your business
Delivering enduring solutions, from inception to completion
Cyber Security Solutions
Cybersecurity Solutions
Cybersecurity solutions are essential for safeguarding sensitive information, preventing cyberattacks, ensuring uninterrupted business operations, meeting regulatory requirements, protecting financial assets, and preserving the organization’s reputation. Without a robust cybersecurity framework, businesses are highly vulnerable to cybercriminals, exposing themselves to significant financial losses, operational disruptions, and potential damage to their reputation.


EDR / XDR / MDR:
EDR (Endpoint Detection and Response) and XDR (Extended Detection and Response) are sophisticated cybersecurity solutions aimed at detecting, investigating, and responding to potential threats across various layers of security. EDR focuses on monitoring and protecting individual endpoints such as laptops and servers, while XDR combines data from multiple security tools, including network, cloud, and endpoint, to deliver a comprehensive and unified defense. Together, EDR and XDR strengthen an organization’s ability to detect advanced threats in real time and reduce their impact.
Solutions provided on EDR/ XDR are from Sentinel One, Crowdstrike and TrendMicro
IDAM Solutions
Identity and Access Management (IDAM), also known as Identity Management (IDM) or IAM (Identity and Access Management), is a set of policies, processes, and technologies designed to securely manage digital identities and regulate access to critical resources within an organization. IDAM solutions are crucial for ensuring that only authorized individuals have access to the appropriate resources at the right time, thereby protecting sensitive information and maintaining organizational security. IDAM Solutions offered are as follows:
- Passwordless
- Multi-Factor Authentication (MFA)
- Biometrics
- Single Sign-On (SSO)
- Adaptive Authentication
IDAM Solutions are provided from the following OEM: Okta, Cisco Duo, RSA, CyberArk, BeyondTrust

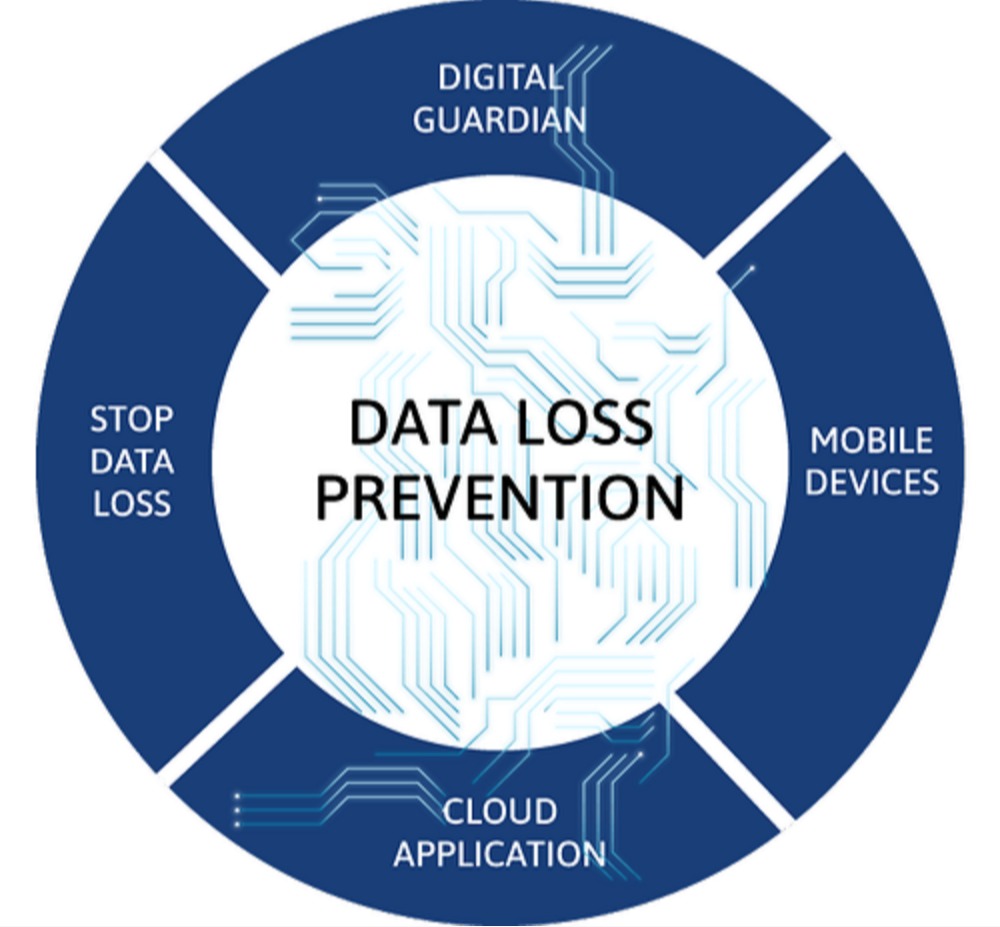
Data Loss Prevention – DLP
Data Loss Prevention (DLP) is essential for protecting sensitive information from unauthorized access, leakage, or theft, whether inside or outside the organization. DLP helps prevent data breaches by monitoring and controlling data transfers across endpoints, networks, and cloud environments. It also ensures compliance with industry regulations like GDPR and HIPAA, minimizing the risk of legal and financial penalties. Furthermore, DLP safeguards intellectual property and helps maintain customer trust, offering peace of mind to organizations and their stakeholders.
DLP is offered from following OEMs: ForcePoint, Cososys, Trellix
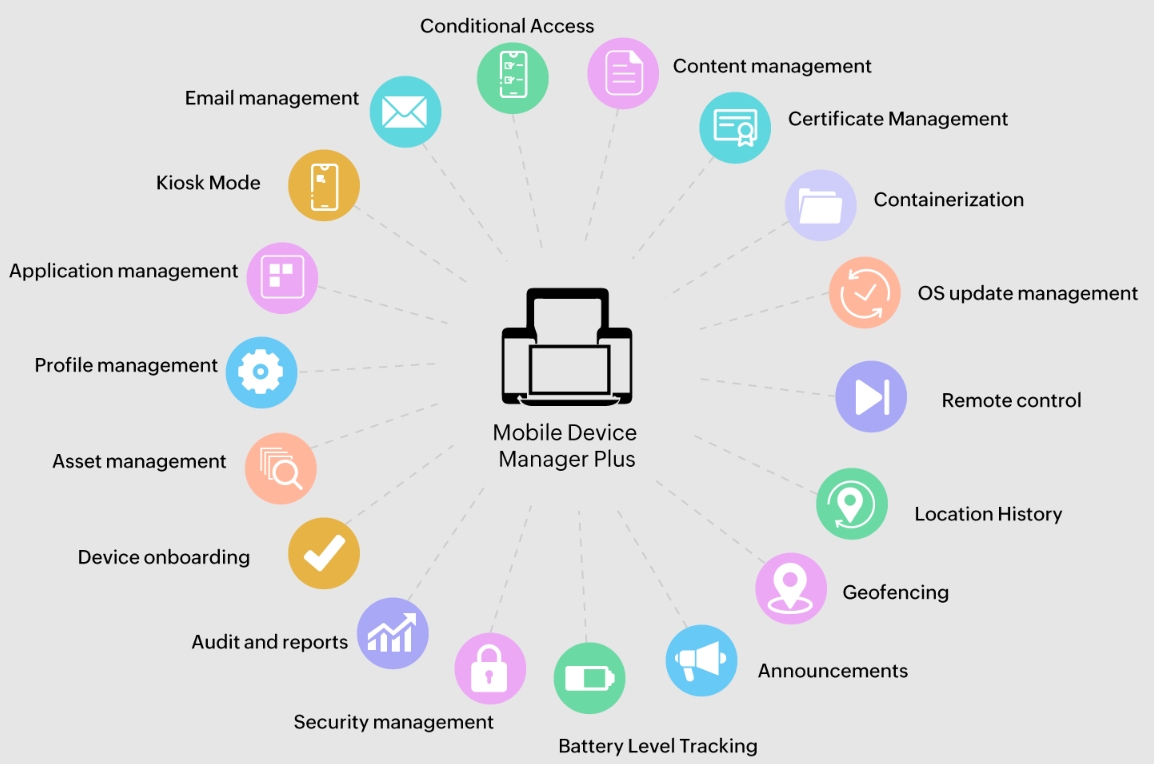
Mobile Device Management (MDM) Solutions
Mobile Device Management (MDM) is crucial for securing and managing mobile devices within an organization, ensuring that smartphones, tablets, and laptops adhere to security standards. MDM allows for remote monitoring, enforcement of security policies, and the ability to wipe data from lost or stolen devices to protect sensitive information. It also simplifies device configuration and software updates, enhancing operational efficiency. By controlling access and usage, MDM helps reduce the risk of data breaches stemming from mobile devices.
We provide MDM from the following OEMs:
ManageEngine , Microsoft Intune, Ivanti UEM, Soti
Firewall / NGFWW

Next-Generation Firewalls (NGFW)
Next-Generation Firewalls (NGFW) offer advanced protection against sophisticated cyber threats by incorporating features like deep packet inspection, application control, and intrusion prevention. They allow organizations to detect and block malicious traffic more effectively than traditional firewalls. NGFWs also provide visibility into encrypted traffic, ensuring that even concealed threats are identified and neutralized. By consolidating multiple security functions into a single device, NGFWs simplify management while enhancing overall network security.
We provide NGFW from PaltAlto, Fortinet, CheckPoint
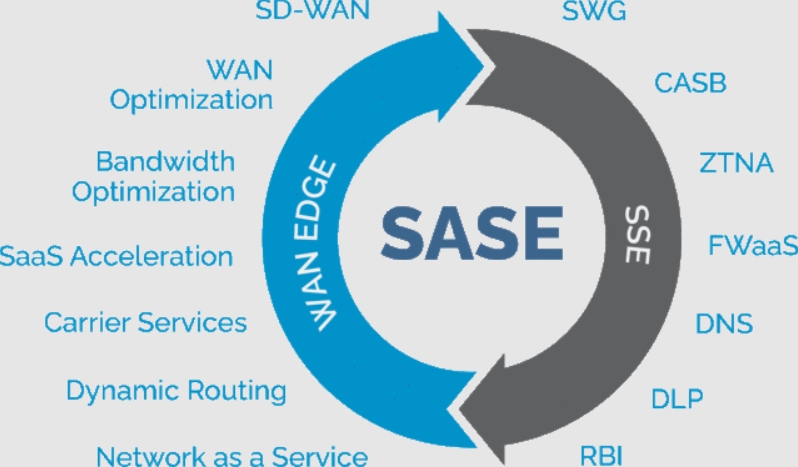
SASE/ SSE - SASE (Secure Access Service Edge) and SSE (Security Service Edge)
SASE (Secure Access Service Edge) is a cloud-native security architecture that combines various networking and security functions, such as SD-WAN, secure web gateways (SWG), firewall-as-a-service (FWaaS), zero-trust network access (ZTNA), and cloud access security brokers (CASB). By integrating these services into a unified, scalable framework, SASE enables organizations to secure their networks while enhancing agility, flexibility, and performance. This approach allows for more efficient management and improved security across distributed environments.
We provide SASE / SSE from NetSkope, Zscaler, PaloAlto
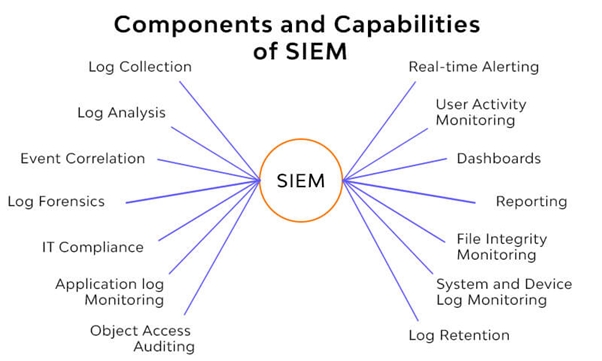
SIEM Solution
SIEM (Security Information and Event Management) and SOAR (Security Orchestration, Automation, and Response
